Code language has been used to safeguard and conceal important messages for thousands of years. As time progressed, complex codes have been created since simple codes are easily decoded. Codes and ciphers are not the same. In code, each word in the message is replaced by a code word or symbol, whereas in cipher, each letter is replaced with another cipher letter or symbol. Ancient languages and scripts were understood using decoding and deciphering techniques. There are over thousands of types of ciphers and codes present. Here we will look at 10 kinds of codes and ciphers.

10 Types of Codes and Ciphers Commonly Used in History
Morse Code
In 1836, the American artist Samuel Morse, with the American physicist Joseph Henry, and Alfred Vail, developed an electrical telegraph system. Morse then developed the forerunner to modern International Morse code. The name "Morse code" is misleading because, this is in fact a cipher not a code. All the letters of the alphabet, number from 0-9 and some punctuation marks have been replaced by dots, dashes or short and long beeps. For example: A is "▪-". Morse code was popularly used when the telegraph was invented. Messages could be sent long-distance electrically using the Morse code via the telegraph. It was not used for concealing message, but transmitting information as a series of clicks, tones or lights.
A skilled observer or listener can directly understand the information without any equipment. It brought in a revolution, since updates from one country could be passed on to other countries immediately. Amateur radio operators used Morse code frequently. A basic understanding is required by pilots and air traffic controllers. SOS, the most common distress signal, recognized internationally is depicted as three dots, three dashes and three dots.
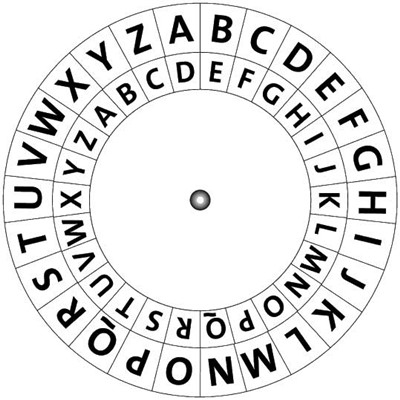
Caesar Shift Cipher
This particular cipher has been named after Julius Caesar, since he used it himself. A cipher was present for each letter of the alphabet, for example ROT1 is one of the ciphers. To decode the message, the person has to be aware which cipher has been used. In G cipher, A becomes G, B becomes H and so on. In Y Cipher, A becomes Y and so on. This particular cipher is not very difficult to decipher and hence secret messages do not remain secret for long. This particular cipher has been used as the basis for creation of more complex ciphers.
Enigma Code
If you ever watched the movie The Imitation Game, you must be familiar with the word "Enigma". The Germans used this sophisticated cipher during the Second World War. It involved using an Enigma machine, which is similar to the type writer. All Germans had the same Enigma machine and the initial wheel configuration of the machine was communicated to all the teams. When a letter was pressed on the machine, a cipher letter lit up on the screen. It got even more difficult when the wheel rotated after certain number of letters, so that the cipher kept on changing. There could be over one hundred trillion possible configurations and hence was difficult to decipher Enigma.
Although it was difficult to decipher, during World War II, Alan Turing, a Cambridge University Mathematician, invented an electromechanical machine that could find settings for the Enigma machine and broke the Germany Enigma. His achievement shortened the war in Europe by 2 to 4 years. The Enigma code was also broken by the Polish.
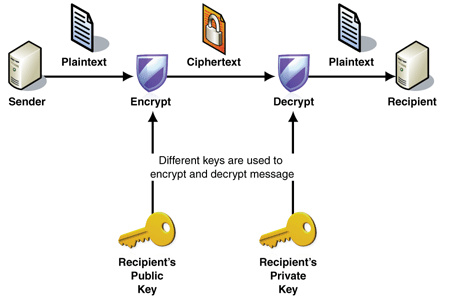
Public-Key Crytography
This is one of the most widely used types of codes or cipher. It is modern and is made of two keys – the private and the public key. The public key is a large number everyone can get. The private key is made of two numbers (apart from 1 and the number itself). These two numbers are multiplied together and can produce the public key. For example, the public key is 1764, the private key can be 36 and 49 (36×49=1764).
It is very secure and is used in emails, bank access details etc. Without the private key, the code cannot be deciphered. It is very difficult to find out the divisors of large numbers. RSA Company ever offered money to people who could find 1 divisors of the numbers they gave.
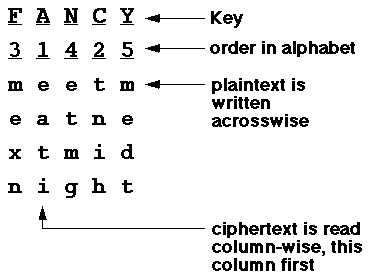
Transposition Cipher
This particular cipher was used during American Civil War and World War I to communicate sensitive messages. The letters of the alphabet are rearranged based on pre-determined key or rule. It could be that all the words in the message are written backwards, or every pair of letters is swapped. If the rearrangement rule is complex, it might seem very difficult to decipher, however, with modern algorithms on the computer, it can be easily deciphered. For example: “the yellow car belongs to him” can become “eht wolley rac sgnoleb ot mih” when written backwards.
Book Cipher
This particular cipher involves the use of some key, essentially in a book. Both the parties should have the same book and the same edition to successfully decipher the code. Locations in the book are used to replace the plain text of the message. The ease of decoding depends on the how well the key has been chosen. Also the book should be inconspicuous and of the genre which is similar to the type of messages required to be sent. The Book Cipher has been widely used in various novels, TV series and movies. In the novel The Valley of Fear, Sherlock Holmes has deciphered a message with the book cipher.
Scytale
This is an old form of cryptography, which was used by ancient Greeks and Spartans during military campaigns. It falls under the transposition cipher and involves a parchment with a message wrapped around a cylinder. The recipient of the message then winds the parchment on a cylinder of the same size to decipher the message. It is fast and not prone to mistakes, however, it is easy to decode. It is said that it was used more of authentication than for encryption.
Steganography
This involves the concealment of a message, image or a file in another message, image or file. The first record of its use is in 1499. Text could be written using invisible ink between visible lines of a text. The benefit of this type is that it does not arouse suspicion like an encrypted message would. There are various ways in which this can be done – physical, digital, social and using puzzles as well. Digital images are used largely for hiding messages as bits. Various modern techniques are available by which steganography can be performed.
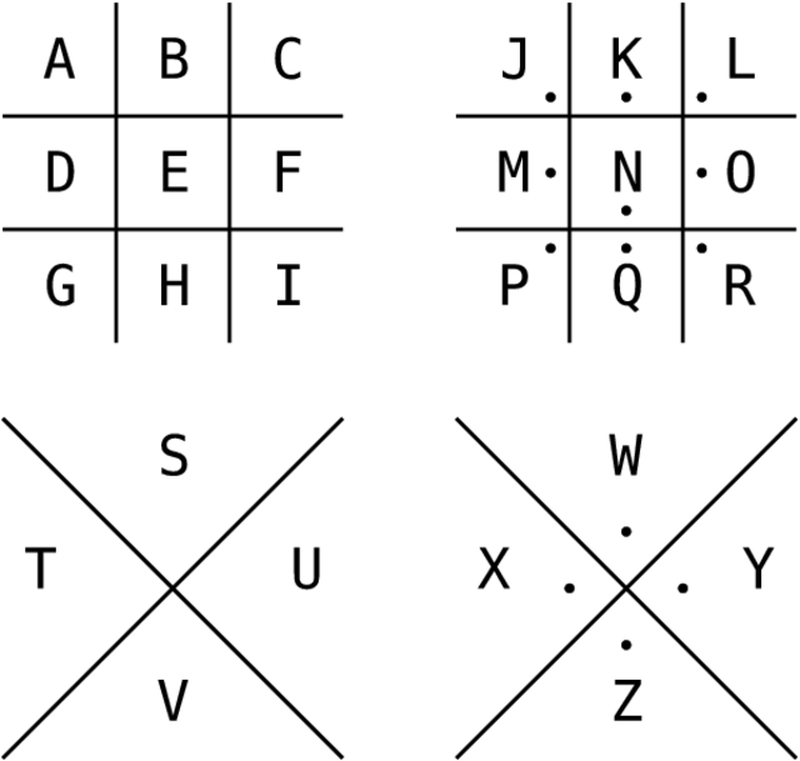
Pigpen Cipher
This is also referred to as Tic-Tac-Toe Cipher, and is fairly simple substitution cipher. The letters of the alphabet are replaced by fragments of a geometrical grid. It is very simple and hence has been used in children’s books of secret writing as well. Although its origin cannot be ascertained, it goes back to the 18th century. The grid and the dots are the core elements of the cipher. The alphabets are arranged in two grids, followed by two Xs. It has been used in various novels –The Lost Symbol by Dan Brown, games like Assasin’s Creed II, TV series – Sherlock, etc.
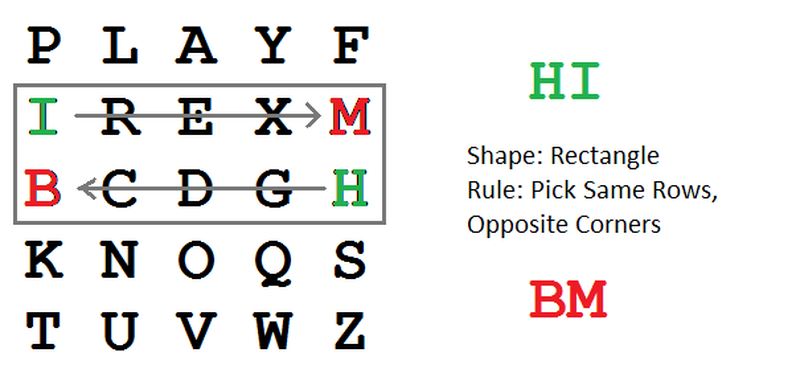
Playfair Cipher
Here we come to the last one on the list of types of codes and ciphers. The Playfair cipher is also known as the Playfair Square. It was the first literal digraph substitution cipher and involves the manual symmetric encryption technique. It was invented by Charles Wheatstone in 1854, but is named after the person who promoted its use. In this type of cipher, pairs of letters are encrypted instead of single letters. Thus it is harder to decipher. It creates 600 possible digraphs as compared to 26 monographs. This cipher also has been used in crossword, novels, movies and audio books. In the film National Treasure: Book of Secrets, the Playfair cipher is used to encode a treasure hunt clue.







View All Comments /Add Comment